Intelligent solutions for your security
Intelligent solutions for your security
We have developed an all-in-one solution where artificial intelligence drones make surveillance of secured area autonomously, with no ground operator presented
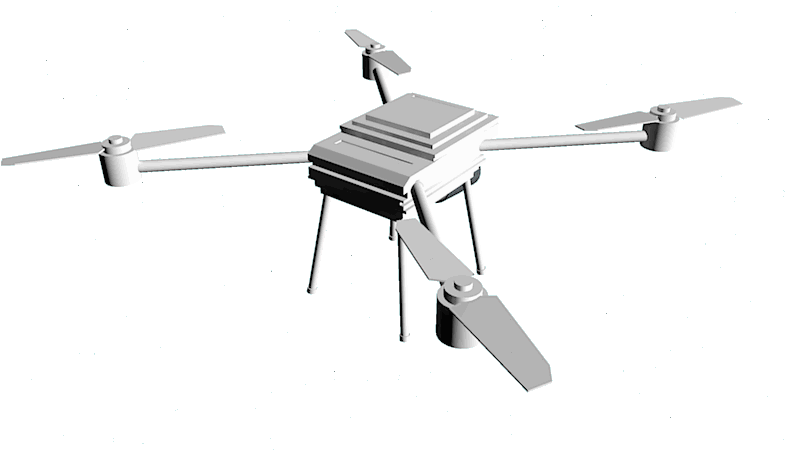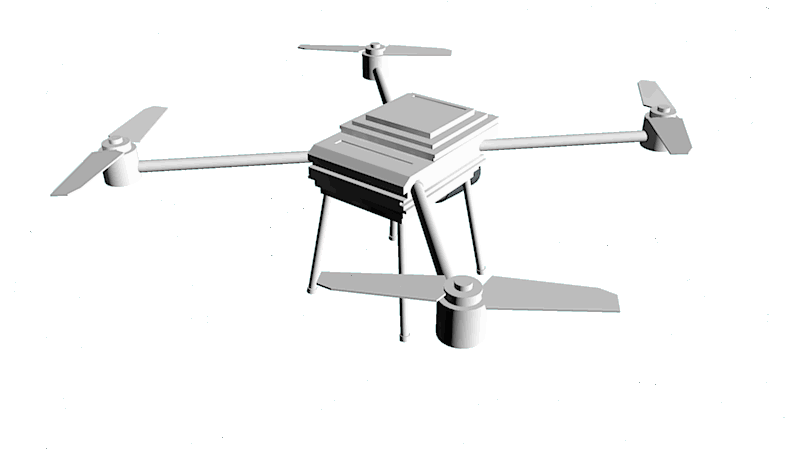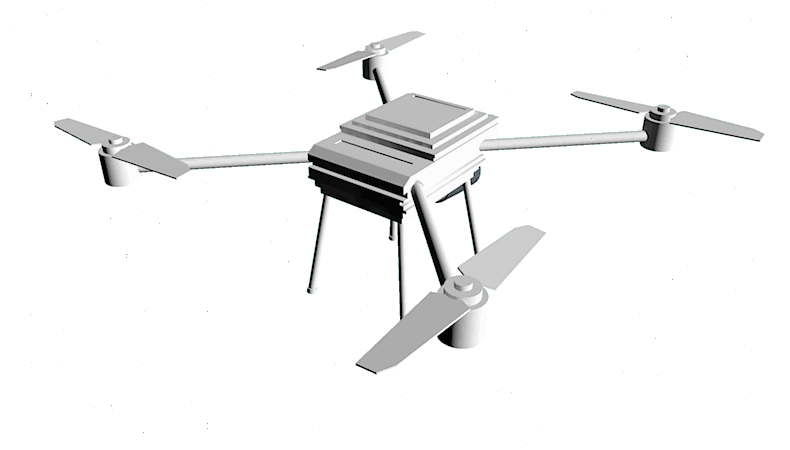
We are multiplying the force of your security staff
Drone, which is moving inside the perimeter, replaces numerous of surveillance cameras because it monitors every inch of the facility.
Drones are performing takeoff, flight and landing according to the pre-programmed schedule and route.
The video stream from copters is transmitted to the operator's monitor. The operator does not need to have any special skills to control the drone


Our clever drone acts like a fast eye on the sky, which is soaring above the suspicious area and transmits video stream to the facility administration

How It Works




The system is building a 3D map of area of the facility or 3D map of the the controlled perimeter.
If something has changed the 3D map is altered automatically



Meanwhile, our software, using artificial intelligence, builds the data base of personal who have access to the monitored area
ALARM!!!
The build in artificial intelligence is constantly monitoring persons, which are have been detected inside the secured site, and if an unknown person is detected an alarm is raised
Drones are performing, inside the property, autonomous patrol missions by schedule or constantly or on alarm, according predefined path, altitude, hover duration, camera direction, etc.
Subscriptions and prices
per month for one device,
billed monthly
| Video archive: | 7 days |
| Number of devices: | 1 |
| Maximum number of records about staff members, which will be stored in database: | 100 |
per month for one device,
billed monthly
| Video archive: | 30 days |
| Number of devices: | 5 |
| Maximum number of records about staff members, which will be stored in database: | 500 |
per month for one device,
billed monthly
| Video archive: | 365 days |
| Number of devices: | 10 |
| Maximum number of records about staff members, which will be stored in database: | 1000 |
The following payment methods are available:
Bank cards, Bank transfer
The Software
Our software receives video stream from drones to continuously monitor the perimeter and detect any unknown individuals who may be present. When an unknown person is detected, the system triggers an alarm to alert security personnel.
Our product is extremely useful in high-security settings, such as private properties, warehouses, power plants and government buildings. The product can help to prevent unauthorized access and enhance security by quickly alerting security personnel to the presence of unknown individuals.
time when employee has been seen by drone
| 7:00 | 8:00 | 9:00 | 10:00 | 11:00 | 12:00 | 13:00 | 14:00 | 15:00 | 16:00 | 17:00 | 18:00 | 19:00 | |
 |
this person has not been caught on camera during 7 hours and 27 minutes
| ||||||||||||
 |

| ||||||||||||
 | |||||||||||||
 | |||||||||||||
 | |||||||||||||
 |
In addition to its safety and security benefits, this type of software can also help businesses to improve their operations and productivity. By providing real-time data on the location of employees, businesses can gain a better understanding of how their employees are utilizing their time and resources. This can help managers to identify any bottlenecks or inefficiencies in their operations and take steps to address them.
The report about an employee
based on the data gathered by drone / drones
 |
Ivan Kravets Chief of development dept. |
Total time, during which this person has been seen
| Today | This week | Last week | During this month |
2 h 53 m |
29 h 47 m |
26 h 53 m |
13 h 12 m |
|
The Reports |
|
|
monday |
tuesday |
wednesday |
thursday |
friday |
saturday |
sunday |
Overall, the use of facial recognition technology in security systems is a powerful tool that can help to enhance security and prevent unauthorized access. By collecting a database of authorized individuals and continuously monitoring the perimeter for unknown individuals, this system provides an extra layer of protection for high-security facilities.